Setting up DMARC shouldn’t feel like decoding a puzzle. And yet, when you look at all the possible tags you could use in a DMARC record, it’s easy to get overwhelmed.
Here’s the good news: You only need three tags to get a fully functioning, secure DMARC record in place.
Let’s break it down without the jargon.
What are DMARC tags?
DMARC tags are the individual components within a DMARC record. Some are mandatory, while others are optional. Each tag defines a certain aspect of DMARC, such as how to handle email that isn’t authenticated or where to send DMARC aggregate reports.
The DMARC standard defines several DMARC tags that can be used in a DMARC record. Some of these tags are required, but most are optional, and several of the tag definitions can be a bit confusing.
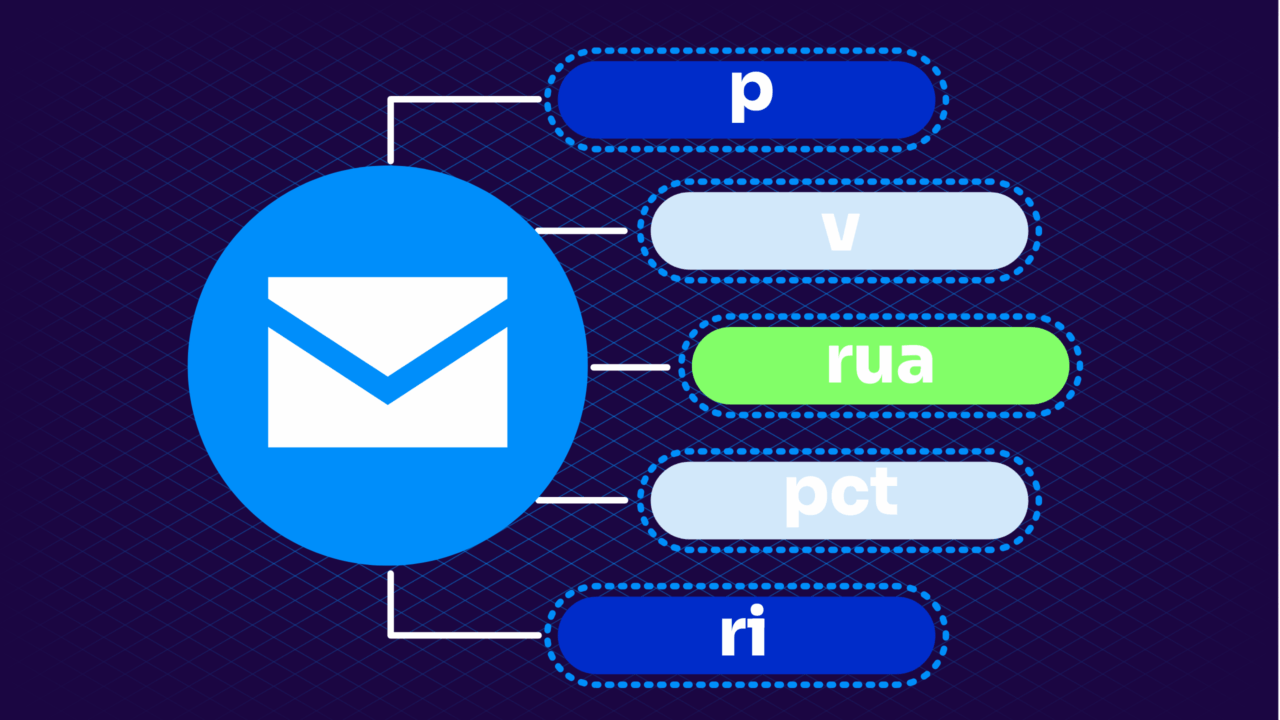
In most cases, a well-formed DMARC record needs to include three tags, while the remaining tags can be ignored. Get these three tags right, and you’ll be able to take advantage of the visibility, control, and anti-phishing benefits that DMARC has to offer:
- V – version tag
- P – policy tag
- RUA – reporting tag
Components of a DMARC TXT record
1. v – version tag
First, every DMARC TXT record needs to begin with the mandatory v or version tag and the corresponding value of “DMARC1.” It’s the presence of this tag that lets receivers know that this DNS TXT record defines a DMARC policy and should be parsed appropriately.
2. p – policy tag
The second tag in a valid DMARC record must be the “p” or policy tag. The “p” tag allows the sending domain to define how a receiver should treat messages purporting to be from this domain (and its subdomains) that fail authentication. It can take one of three values:
- p=none: The sending domain is in test mode. An email that fails authentication will be reported, but no additional action will be taken. This is a good place to start, but domains at p=none get very few of the benefits of DMARC.
- p=quarantine: Receivers are asked to quarantine messages that fail authentication. Typically, the message is marked as spam.
- p=reject: Receivers are asked not to deliver failing messages to the recipient at all. Some receivers honor this request, while other receivers just mark failing messages as spam.
3. rua
The only other value that generally needs to be included in every DMARC record is the rua tag. The rua tag contains a comma-separated list of mail-to URLs that define where receivers should send aggregate reports.
Aggregate reports are the method receivers use to give feedback to domain owners on the messages they’re seeing that claim to be from the domain. These reports are zipped XML documents containing aggregated information on the source IP addresses and authentication status for all the messages in a given period (typically a day).
When properly analyzed by a service like Valimail, these reports can provide the domain owner with a comprehensive view of which servers and third-party services are sending messages on the domain owner’s behalf, as well as any potential abuse of the domain by phishers.
Without aggregate reports, you’re flying blind. Moving to a p=quarantine or p=reject policy becomes very unsafe because legitimate email may be unknowingly blocked. While including a rua tag is not mandatory from a specification perspective, we recommend including it consistently.
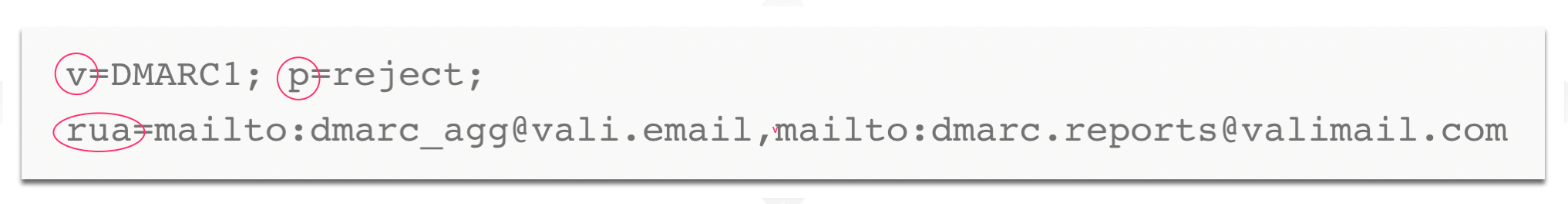
Sample DMARC records with tags
For most DMARC records, these values are all you need. A typical TXT record might look like this, where the email address in the rua is replaced with the reporting address for your domain:
Curious what your DMARC policy looks like and what tags you've used? Use Valimail's free domain checker to discover your tags:Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Check your
domain now
Enter your domain to see if it’s vulnerable to spoofing or if others are sending emails on your behalf. Instantly check your DMARC, SPF, and BIMI status with a detailed security report.
You’re not fully protected, learn more here.
Your Domain
Not protected AGAINST IMPERSONATION ATTACKS
DMARC NOT AT ENFORCEMENT
exampledomain1.com
Authentication Status for January 10, 2025
DMARC at Enforcement
SPF Record Configured
BIMI Ready
exampledomain1.com
Authentication Status for January 10, 2025
DMARC at Enforcement
SPF Record Configured
BIMI Ready
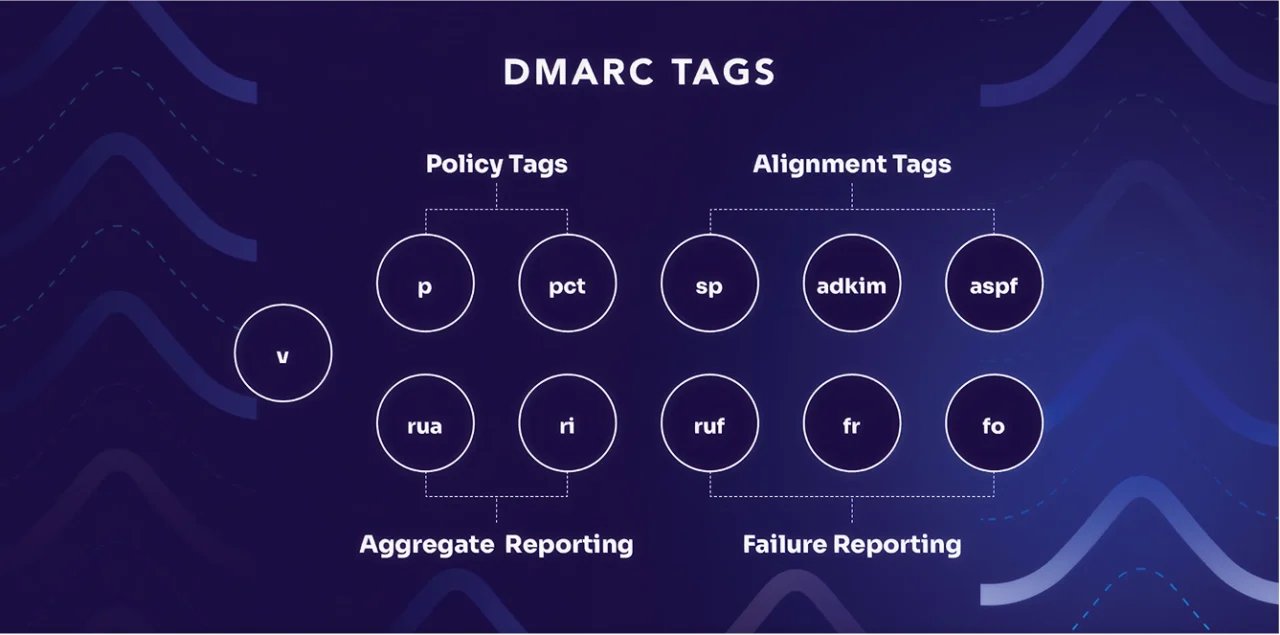
Optional DMARC tags
There are more than three DMARC tags, but those are the only three that are absolutely required to set up your DMARC policy. However, there are other DMARC tags that are optional. You don’t need to include all of these to benefit from DMARC. In fact, using too many too early can create confusion or misconfiguration. While you don’t need to use them, they may be helpful in some instances:
| Tag | Name | Required | Description |
|---|---|---|---|
v | Version | Yes | Must be set to DMARC1 to identify the record as a DMARC policy. |
p | Policy | Yes | Tells receivers what to do with messages that fail DMARC (none, quarantine, or reject). |
rua | Aggregate reports | Yes | Specifies where to send DMARC aggregate reports (mailto: URL). Not technically required, but essential for visibility. |
ruf | Forensic reports | No | Sends detailed (and potentially sensitive) failure reports to a designated address. Rarely used today. |
pct | Percentage | No | Applies policy to only a portion of your messages (e.g., pct=50 applies policy to half of traffic). |
sp | Subdomain policy | No | Defines a different policy for subdomains than the main domain. |
aspf | SPF alignment mode | No | Sets strict or relaxed alignment for SPF (r or s). |
adkim | DKIM alignment mode | No | Sets strict or relaxed alignment for DKIM (r or s). |
fo | Forensic options | No | Controls when forensic reports are sent (used with ruf). |
rf | Report format | No | Specifies format of failure reports (usually left at default: afrf). |
ri | Report interval | No | Suggests how often (in seconds) to send aggregate reports. Most receivers default to 86400 (24 hours). |
For most organizations, the required tags (v, p, and rua) are all you need to:
- Start receiving feedback
- Monitor your domain’s mail streams
- Begin your journey toward full DMARC enforcement
Advanced tags like aspf, pct, or sp are useful in more complex deployments, but they’re not necessary for a standard DMARC rollout.
If you’re unsure what to include, keeping it simple is the best path, and Valimail can help you automate and manage this without the guesswork.
Easily manage your DMARC tags
Make DMARC simple and safe to enforce.
Valimail simplifies email authentication. Our platform analyzes your DMARC reports, identifies trusted senders, and guides you step by step toward full enforcement with no broken email, no guesswork.
Start by signing up for Valimail Monitor and get free visibility and more management of your DMARC tags.
Frequently asked questions about DMARC tags
Q: Should I use ruf for forensic reports?
In most cases, no. Forensic (ruf) reports are less widely supported, and they may contain sensitive data. Unless you have a very specific use case and know how to handle that data securely, it’s better to rely on aggregate reports (rua) and a platform like Valimail to interpret them.
Q: What happens if my DMARC record is missing required tags?
If your DMARC record is missing the v=DMARC1 or p= tag, inbox providers will ignore it entirely. That means no policy enforcement, no reports, and no visibility. Essentially, it’s as if the record doesn’t exist. Always double-check that your record includes at least those two.
Q: What does the pct tag do in a DMARC record?
The pct (percentage) tag lets you apply your DMARC policy to only a portion of your email traffic. For example, pct=50 means only 50% of failing messages will be affected by the policy. This can be useful when gradually moving from none to quarantine or reject. However, most inbox providers don’t consistently support partial enforcement, so it’s often safer to use alternative methods to phase in enforcement.